Security Audit.
A complete and detailed security evaluation of your smart contract that identifies flaws and suggests solutions.

What is a security audit report ?
Our audit reports are unique and contain multiple thorough analyses. At the beginning of the report, we will address the overall security level of the project. In the later part, the report will contain detailed information of any discovered vulnerabilities and classify them by severity (Critical, High, Medium, and Low), as well as provide recommendations for possible solutions.
How a Smart Contract Audit works ?
Our security audit platform evaluates smart contracts for vulnerabilities and certifies their behavior with respect to a custom function specification.
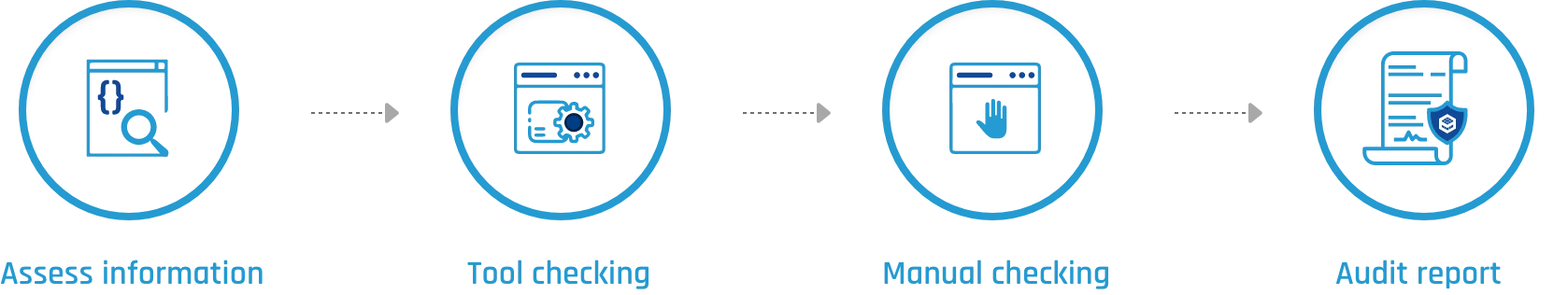
Our security audit including these steps:
- First we assess your smart contract's business logic and agree on the security attributes to be tested.
- Use tools to analyze smart contracts before deploying them to find vulnerabilities open to exploitation. (Formal Verification Engine)
- Our team members do a manual check to look for any issues. (Expert Review)
- We provide a detailed report that includes information on vulnerabilities, mitigation recommendations, and alternatives for ongoing monitoring.
Frequently Asked Question
What will I find in the audit report ?
Our audit reports are divided into three sections. The project's overall security level is the first part. The second section contains detailed information on any discovered vulnerabilities, as well as a severity classification. The final section contains our suggestions for possible solutions.
Is the report private ?
Yes. We send the report to your team in confidence so that they can address the issues we discovered. It's optional to publish the report after your team has resolved the issues, but it's strongly encouraged as a way to contribute to the ecosystem's security. We can collaborate on a disclosure strategy with you.
What is the goals and objectives of audit ?
Objectives of the assessment are: check whether the smart contract is vulnerable to known attacks, verify that it doesn’t have any logic or access control issues, and verify that it is compliant to Solidity Code Style Guide. The goal of the audit is to find and fix security issues to protect the application from hacker attacks
The limitation of the audit team in the audit process
- The operational impact to the networks will be maintained to the minimum but coordinated with the client
- No active backdoor or Trojans will be installed
- No client data will be copied, modified, or destroyed.